How Hackers Use Binary Padding to Outsmart Sandboxes
By A Mystery Man Writer

How Hackers Use Binary Padding to Outsmart Sandboxes

How Hackers Use Binary Padding to Outsmart Sandboxes

How can Advanced Sandboxing Techniques Thwart Elusive Malware? - Wiadomości bezpieczeństwa

Gray Hat Hacking: The Ethical Hacker's Handbook [2nd edition] 0071595538, 0071495681, 1211471691, 9780071595537
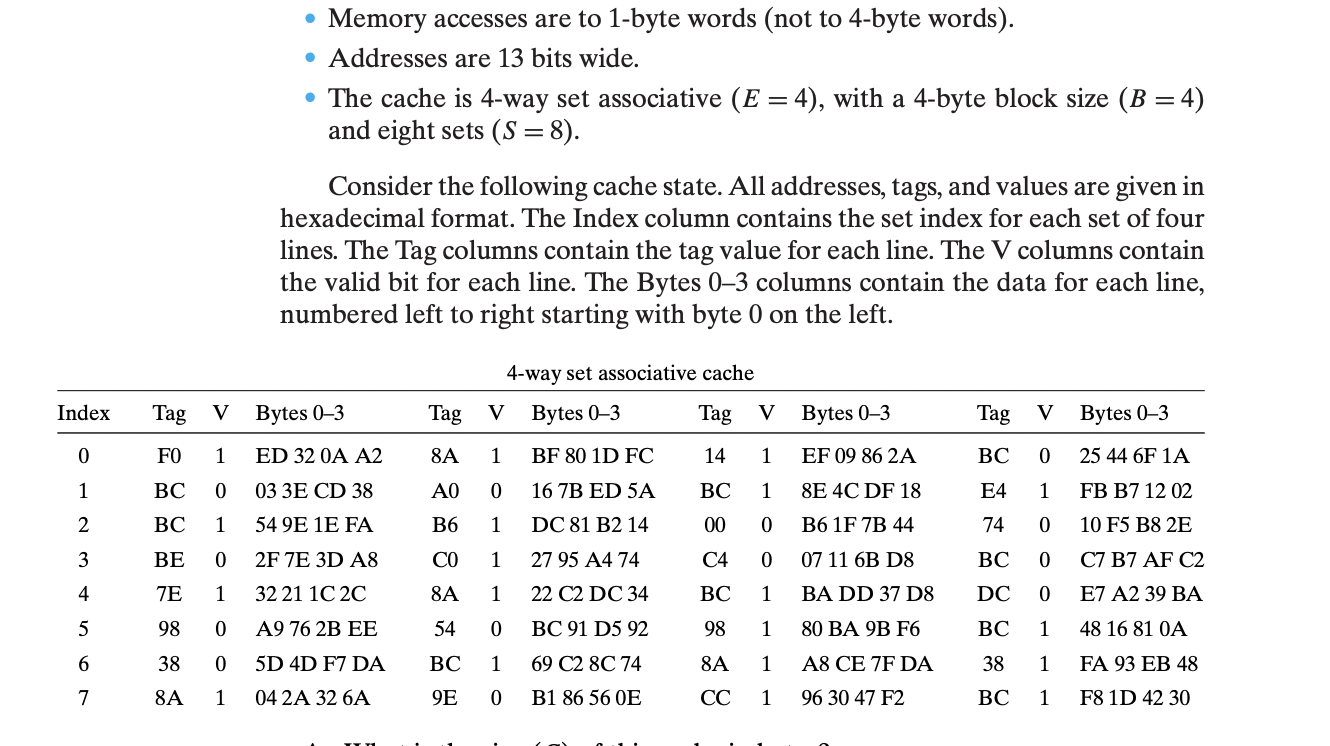
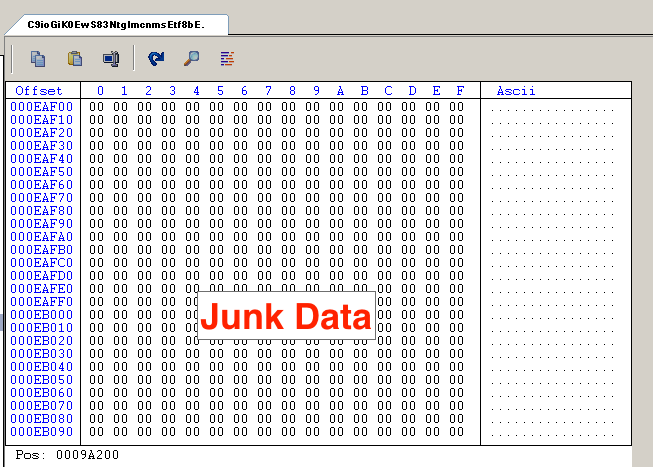
Solved Memory Address Is Always In Terms Of, 43% OFF

Detect Malware Associated with the Most Exploited CVEs - Intezer

Emre KISA على LinkedIn: How Hackers Use Binary Padding to Outsmart Sandboxes and Infiltrate Your…

Intezer - Blog

Emre KISA on LinkedIn: Indirect prompt injection, have you heard

Itai Tevet on LinkedIn: How Hackers Use Binary Padding to Outsmart Sandboxes and Infiltrate Your…

Emre KISA on LinkedIn: If only i had a dollar for everytime i was asked for this 🙄

5 Ways Hackers Evade Organizations' Sandboxes
- What is Padding in Convolutional Neural Network's(CNN's) padding
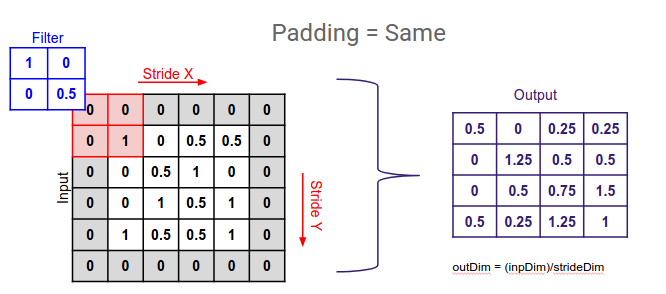
- Guide to Different Padding Methods for CNN Models
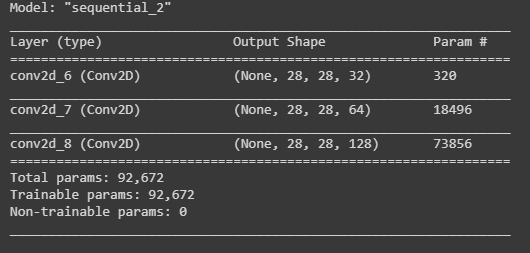
- Select without padding - Codesandbox

- Convolution operation without padding (a), and with same zeropadding

- conv neural network - Convolutional Layers: To pad or not to pad? - Cross Validated





