Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
By A Mystery Man Writer
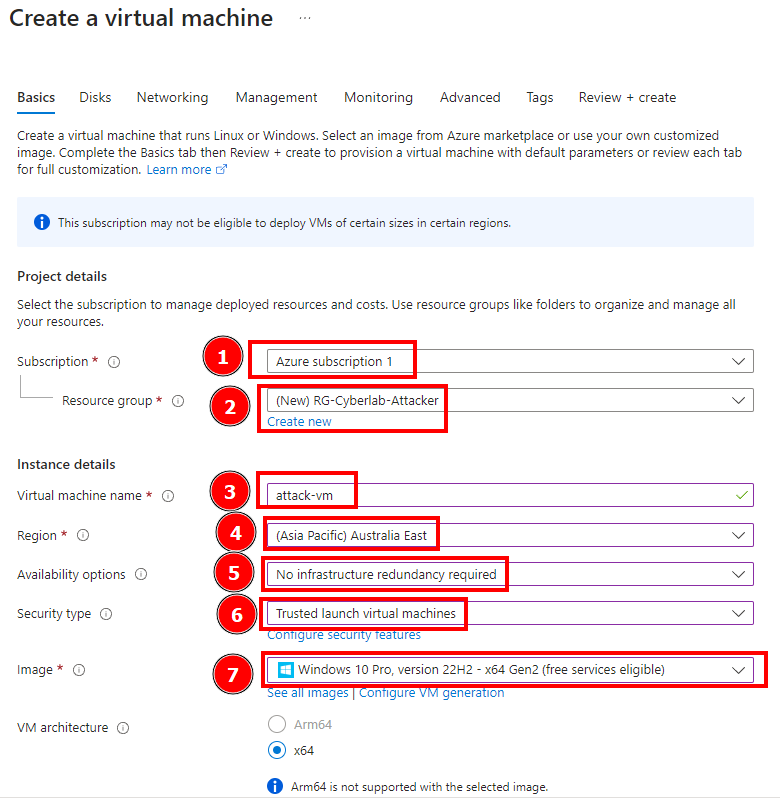
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…

Denial of Service Attack Project
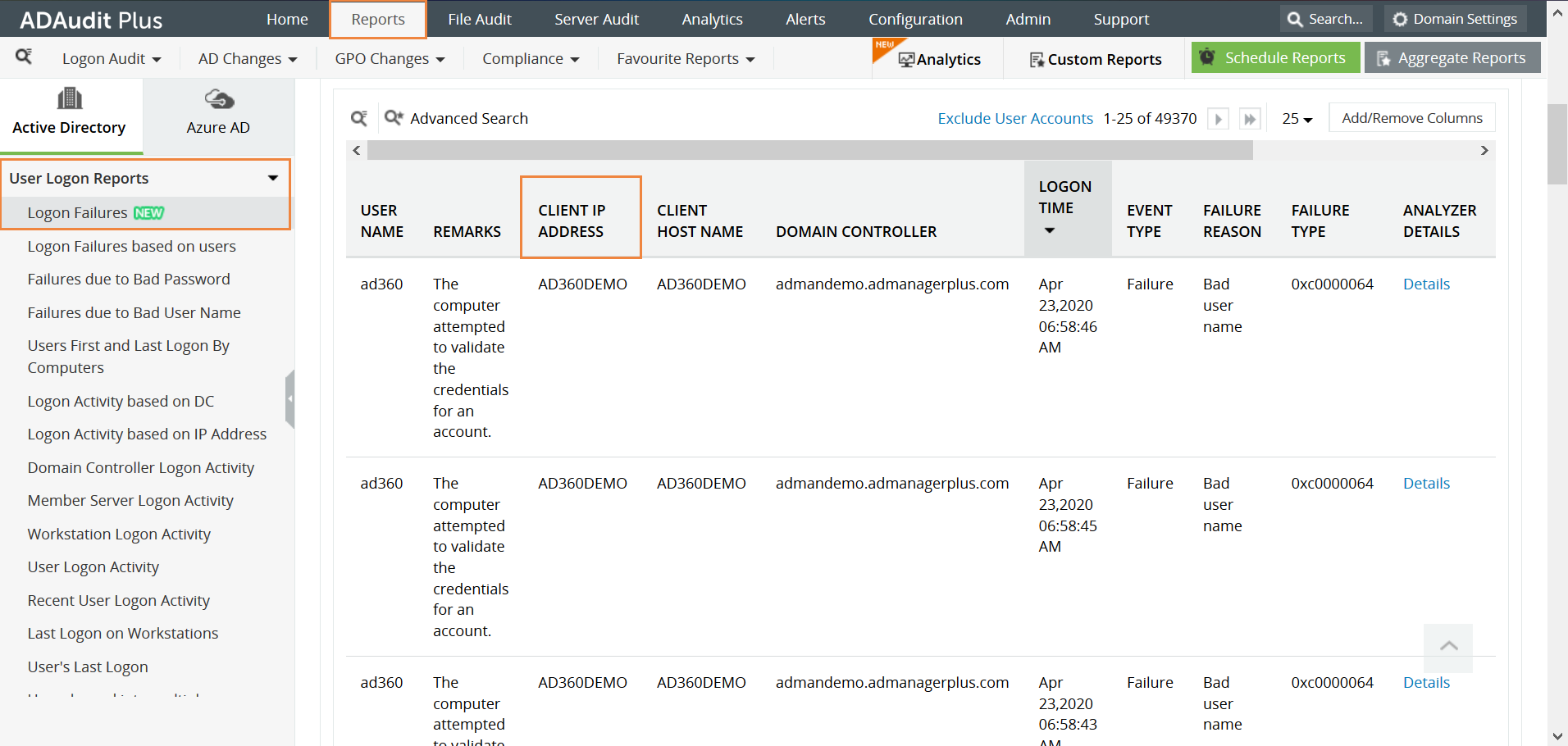
How to find the source of failed login attempts

Workflow of Failed login attempts

How to Detect and Analyze DDoS Attacks Using Log Analysis

PDF) Towards Automated Attack Simulations of BPMN-based Processes
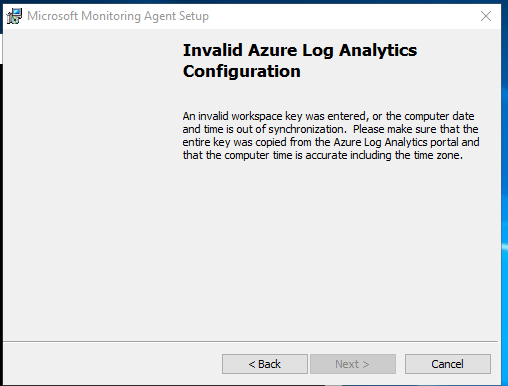
Issue With OMS Gateway - Microsoft Q&A
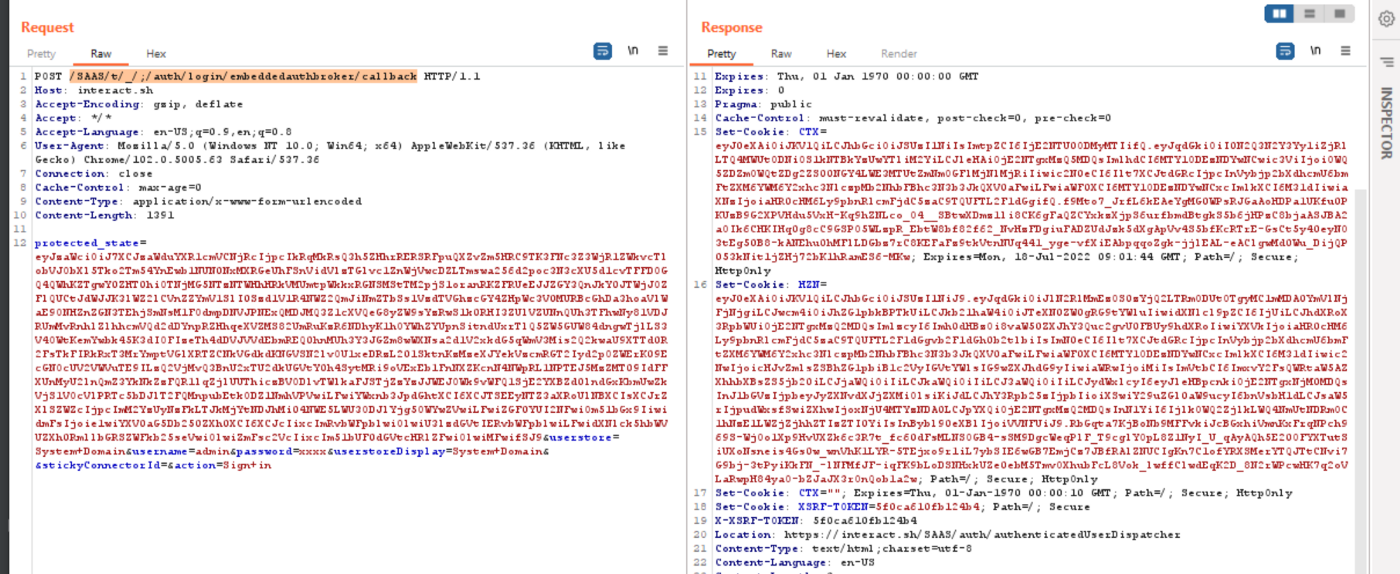
Public Exploit Available for Critical VMware Bug CVE-2022-31656 - Security Investigation
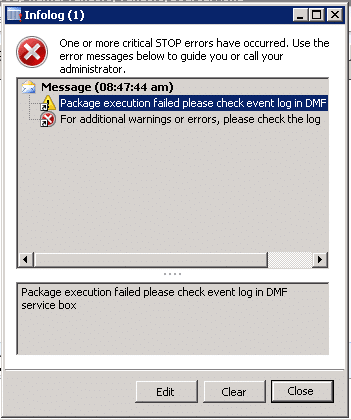
Dynamics AX DIEF error: Package Execution Failed Please Check Event Log in DMF Service Box

What are breach and attack simulations? - IBM Blog
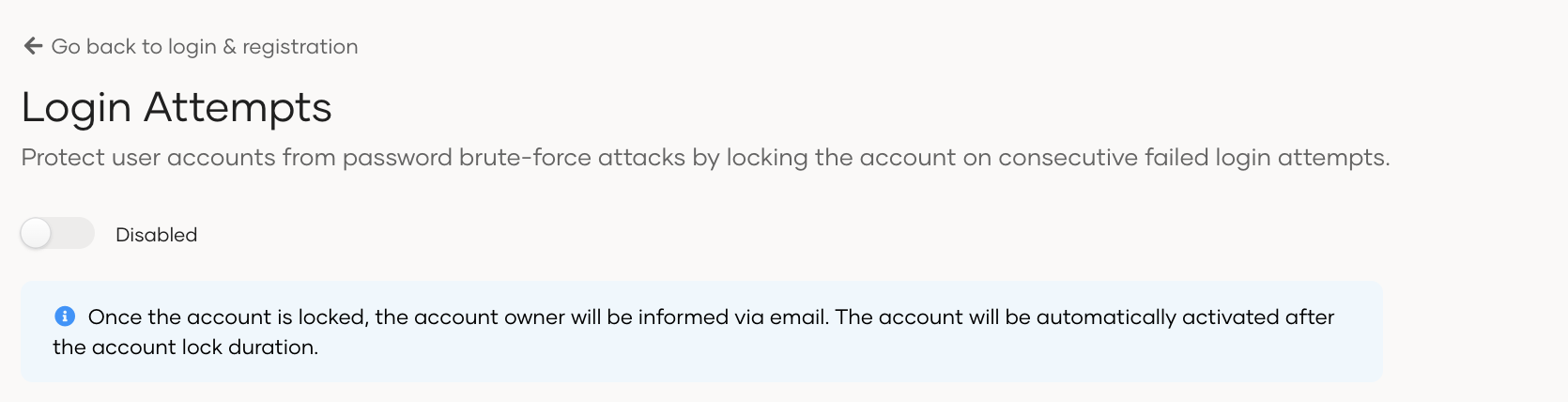
Configure login-attempts security

PDF) POIROT: Aligning Attack Behavior with Kernel Audit Records for Cyber Threat Hunting

Portswigger: Exploiting vulnerabilities in LLM APIs

Part 9: Microsoft Sentinel Incident Response., by Duyet Bui
- Transparent People Walking Png - Old Man Walking Png, Png Download - vhv

- Disha Patani Stuns in Calvin Klein Lingerie Disha Patani Stuns in Calvin Klein Lingerie

- Mneostt X Large Mens Simple Personality Sexy Mini Thong Open Mouth Underwear T Pants Mens Sheer Underwear, Beige, One Size : : Clothing, Shoes & Accessories

- Eytino Hooded Cardigan Sweaters for Women Long Sleeve Button Down Knit Sweater Coat Outwear with Pockets

- Body Bliss (@bodyblisslasers) • Instagram photos and videos




