Attackers can force Echos to hack themselves with self-issued commands

By A Mystery Man Writer
Popular “smart” device follows commands issued by its own speaker. What could go wrong?

OWASP Top Ten Part 1. Today we will be looking at the first 5…, by Angel Mercado, Learning CyberSecurity

Mapping vulnerabilities in echo using alexa skills

Attackers can force Echos to hack themselves with self-issued commands
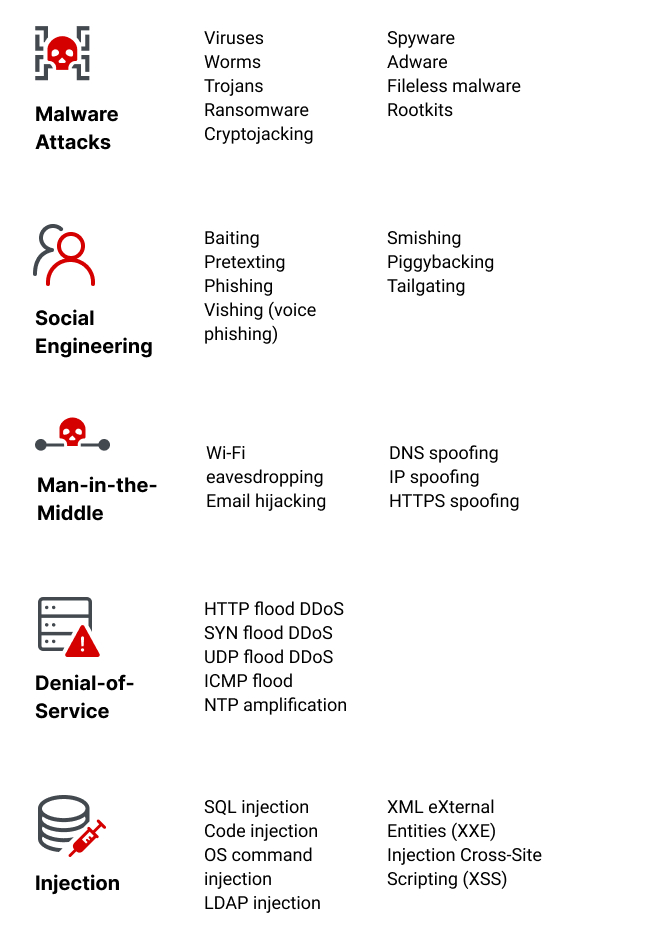
Cybersecurity Threats, Types & Sources
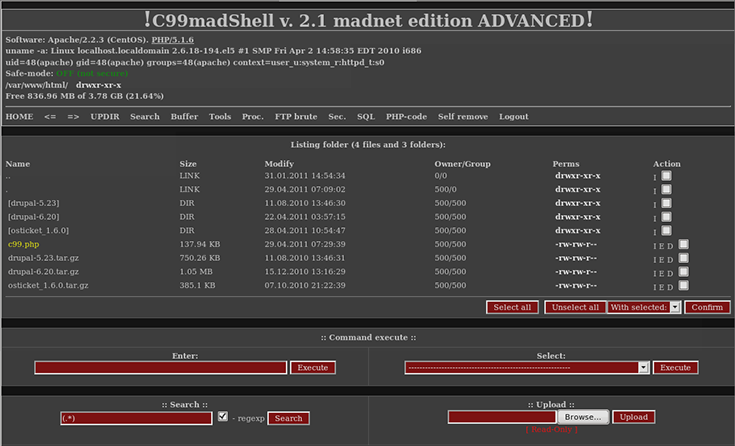
What is a Backdoor Attack, Shell & Trojan Removal

The Mirai Confessions: Three Young Hackers Who Built a Web-Killing Monster Finally Tell Their Story

A survey on security analysis of echo devices - ScienceDirect
How would you hack me? As someone trying to protect themselves, what could I do that might make it harder/not worth it? (I know 100% secure is impossible) How do you personally
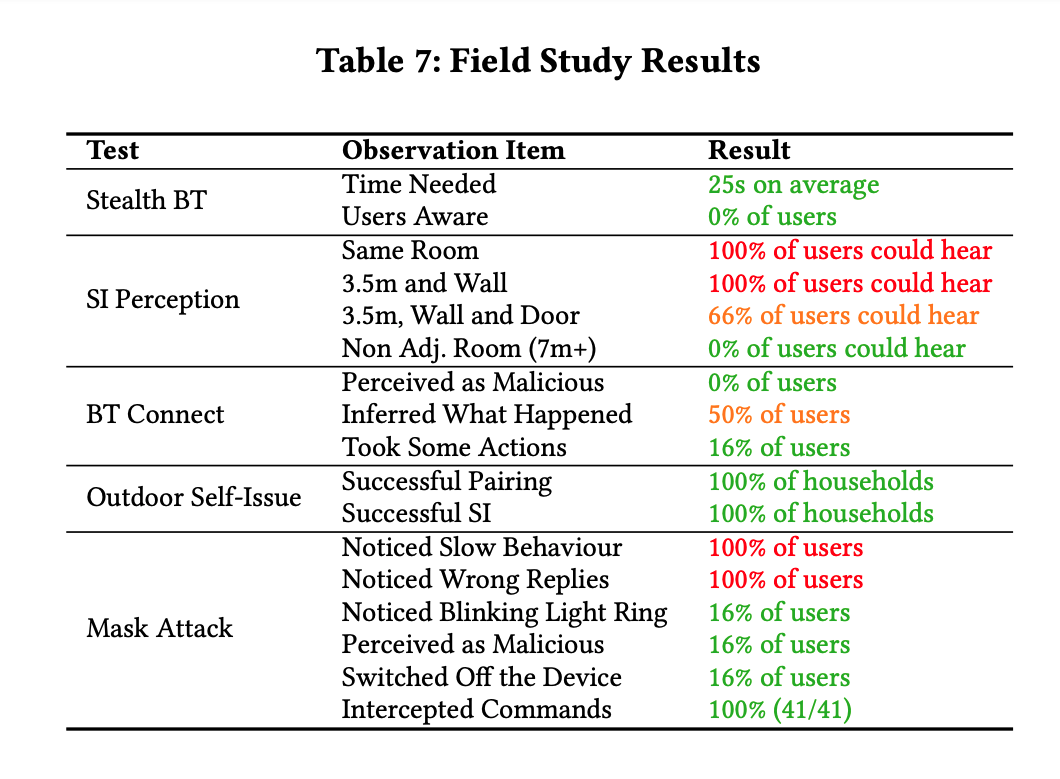
Attackers can force Echos to hack themselves with self-issued commands
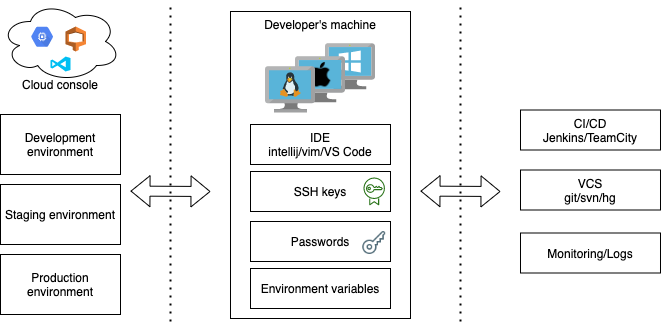
Deep dive into Visual Studio Code extension security vulnerabilities

Computer Systems Security: Planning for Success
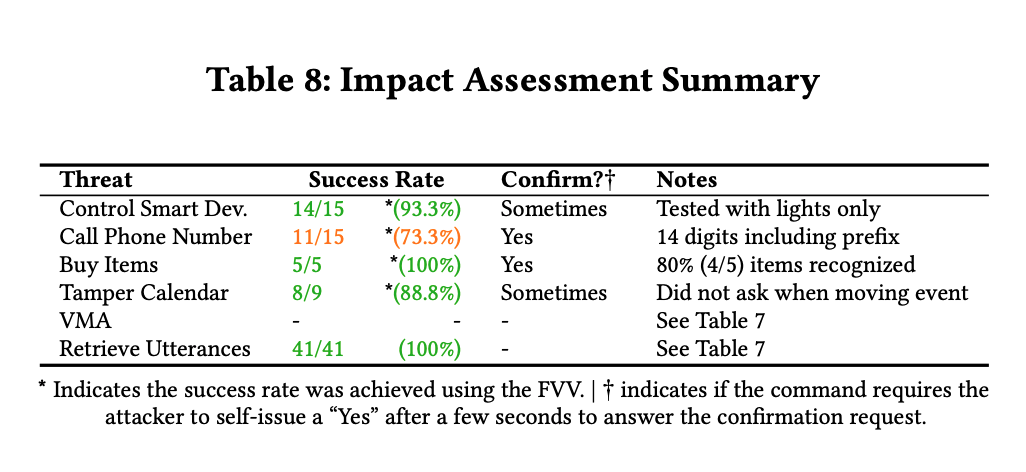
Attackers can force Echos to hack themselves with self-issued commands
- Alexa: How to start a smart home - The Verge
/cdn.vox-cdn.com/uploads/chorus_asset/file/24720645/236676_06_How_to_start_a_smart_home_using_Amazon_Alexa_SHaddad.jpg)
- Echo (4th Gen) with Premium Sound, Smart Home Hub, and

- Echo Dot with Clock (5th Gen, 2022 Release) Compact Smart Speaker with Alexa - Glacier White

- Alexa: Everything you need to know about the digital assistant

- Echo Studio Smart Speaker with Alexa in Charcoal B07G9Y3ZMC





